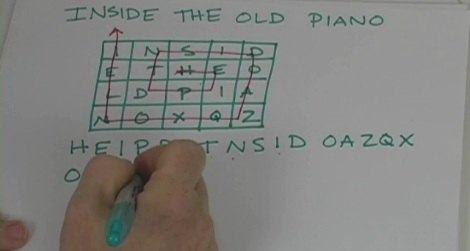
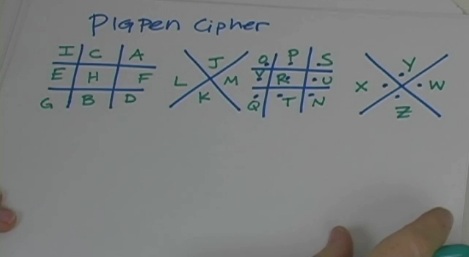
Cryptography is the writing and decoding of secret messages, called ciphers. Now for governments these secret ciphers are a matter of national security. They hire special cryptanalysts who work on these ciphers using cryptanalysis. The secret is, solving substitution ciphers can be pretty entertaining! Ciphers are published daily in newspapers everywhere. If you practice encoding and decoding ciphers, you too can become a really great cryptanalyst.
In this video, I’ll show you how to use the Rail Fence Cipher. Before you start, say this three times fast: cryptanalysts use cryptanalysis to crack ciphers!
Please login or register to read the rest of this content.